The NIST Cybersecurity Framework and the FTC

The NIST Cybersecurity Framework and the FTC
We often get the question, “If I comply with the NIST Cybersecurity Framework, am I complying with what the FTC requires?” From the perspective of the staff of the Federal Trade Commission, NIST’s Cybersecurity Framework is consistent with the process-based approach that the FTC has followed since the late 1990s, the 60+ law enforcement actions the FTC has brought to date, and the agency’s educational messages to companies, including its recent Start with Security guidance. First, a little background.
How did the Cybersecurity Framework come about?
In February 2013, President Obama issued Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which called on the Department of Commerce’s National Institute of Standards and Technology (NIST) to develop a voluntary risk-based Cybersecurity Framework for the nation’s critical infrastructure—that is, a set of industry standards and best practices to help organizations identify, assess, and manage cybersecurity risks. NIST issued the resulting Framework in February 2014.
What is the Cybersecurity Framework?
 The Framework provides organizations with a risk-based compilation of guidelines that can help them identify, implement, and improve cybersecurity practices. The Framework does not introduce new standards or concepts; rather, it leverages and integrates cybersecurity practices that have been developed by organizations like NIST and the International Standardization Organization (ISO).
The Framework provides organizations with a risk-based compilation of guidelines that can help them identify, implement, and improve cybersecurity practices. The Framework does not introduce new standards or concepts; rather, it leverages and integrates cybersecurity practices that have been developed by organizations like NIST and the International Standardization Organization (ISO).
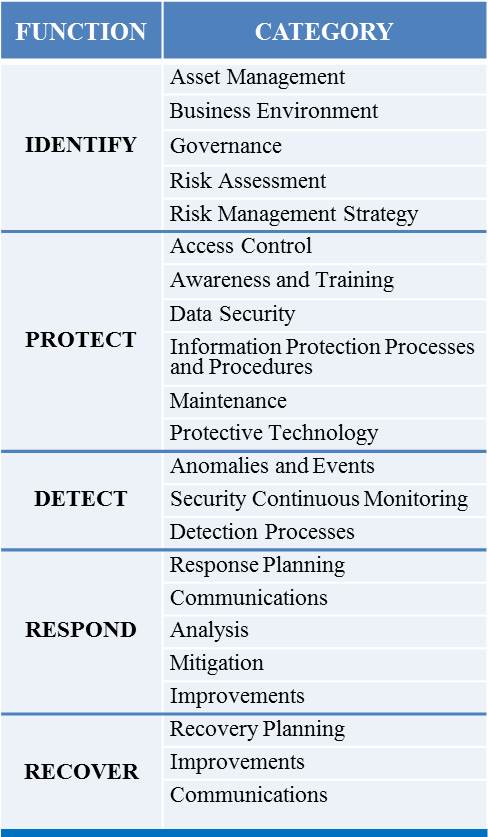
The Framework terms this compilation of practices as the “Core.” This Core is composed of five concurrent and continuous functions—Identify, Protect, Detect, Respond, and Recover—that provide a strategic view of the lifecycle of an organization’s management of cybersecurity risk. Each function is further divided into categories tied to programmatic needs and particular activities. In addition, each category is broken down into subcategories that point to informative references. Those references cite specific sections of standards, guidelines, and practices that illustrate a method to achieve the outcomes associated with each subcategory.
The five functions signify the key elements of effective cybersecurity. Identify helps organizations gain an understanding of how to manage cybersecurity risks to systems, assets, data, and capabilities. Protect helps organizations develop the controls and safeguards necessary to protect against or deter cybersecurity threats. Detect are the steps organizations should consider taking to provide proactive and real-time alerts of cybersecurity-related events. Respond helps organizations develop effective incident response activities. And Recover is the development of continuity plans so organizations can maintain resilience—and get back to business—after a breach.
The Framework breaks down each of these functions into additional categories and then provides helpful guidance. For example, as the chart above shows, the Identify function has five categories: Asset Management; Business Environment; Governance; Risk Assessment; and Risk Management Strategy. Under Governance, one of the four subcategories is that an organization should establish an organizational security policy. The subcategory points organizations to standards such as COBIT, ISA, ISO/IEC, and NIST SP 800-53 Rev. 4 for information on how to implement a policy.
As the Framework recognizes, there’s no one-size-fits-all approach to managing cybersecurity risk. Because organizations have unique risks—different threats, different vulnerabilities, different risk tolerances—their approaches to risk management will vary. But that’s the benefit of the Framework: It’s not a checklist, but rather a compilation of industry-leading cybersecurity practices that organizations should consider in building their own cybersecurity programs. For most organizations, critical infrastructure or not, the Framework may be well worth using solely for its stated goal of improving risk-based security. But it also can deliver additional benefits—for example, encouraging effective collaboration and communication with company executives and industry organizations. That’s because the Core provides a common language regarding cybersecurity issues that can help facilitate important discussions between an organization’s IT staff and its business people, some of whom may tune out when they hear technical terminology.
How does the Framework relate to the FTC’s work on data security?
As the nation’s consumer protection agency, the FTC is committed to protecting consumer privacy and promoting data security in the private sector. The FTC has undertaken substantial efforts for well over a decade to promote data security in the private sector through civil law enforcement, business outreach and consumer education, policy initiatives, and recommendations to Congress to enact legislation in this area. Section 5 of the FTC Act is the primary enforcement tool that the FTC relies on to prevent deceptive and unfair business practices in the area of data security. Since 2001, the FTC has settled some 60 cases against companies the FTC alleges failed to provide reasonable protections for consumers’ personal information.
From the outset, the FTC has recognized that there is no such thing as perfect security, and that security is a continuing process of detecting risks and adjusting one’s security program and defenses. For that reason, the touchstone of the FTC’s approach to data security has been reasonableness—that is, a company’s data security measures must be reasonable in light of the volume and sensitivity of information the company holds, the size and complexity of the company’s operations, the cost of the tools that are available to address vulnerabilities, and other factors. Moreover, the FTC’s cases focus on whether the company has undertaken a reasonable process to secure data.
With that bit of background on the FTC’s data security program, let’s get back to the question, “If I comply with the Framework, am I complying with what the FTC requires?” The Framework is not, and isn’t intended to be, a standard or checklist. It’s meant to be used by an organization to determine its current cybersecurity capabilities, set individual goals, and establish a plan for improving and maintaining a cybersecurity program, but it doesn’t include specific requirements or elements. In this respect, there’s really no such thing as “complying with the Framework.” Instead, it’s important to remember that the Framework is about risk assessment and mitigation. In this regard, the Framework and the FTC’s approach are fully consistent: The types of things the Framework calls for organizations to evaluate are the types of things the FTC has been evaluating for years in its Section 5 enforcement to determine whether a company’s data security and its processes are reasonable. By identifying different risk management practices and defining different levels of implementation, the NIST Framework takes a similar approach to the FTC’s long-standing Section 5 enforcement.
Indeed, the alleged lapses the FTC has challenged through its law enforcement actions correspond well with the Framework’s five Core functions. Let’s review each of the Framework’s functions more fully.
Identify. The purpose of the Identify function is to develop an understanding of cybersecurity risks to systems, assets, data, and capabilities, which in turn helps organizations focus and prioritize their security efforts, consistent with their risk management strategy and business needs.
The FTC has brought a number of cases alleging that companies had failed to take appropriate action to assess security risks and develop plans to address them. These same types of activities fall within the Framework’s Identify function. For example, in the complaints against CVS Caremark Corporation and Petco Animal Supplies, Inc., the FTC alleged that those companies failed to implement policies and procedures to safeguard consumers’ information. These allegations align with the Framework’s guidance on establishing an organizational information security policy.
 Likewise, in the complaints against HTC America, Inc. and TRENDnet, Inc., the FTC alleged that the companies did not have a process for receiving, addressing, or monitoring reports about security vulnerabilities. These allegations are consistent with the Framework’s guidance that companies should consider having a method for receiving threat and vulnerability information from information-sharing forums and sources.
Likewise, in the complaints against HTC America, Inc. and TRENDnet, Inc., the FTC alleged that the companies did not have a process for receiving, addressing, or monitoring reports about security vulnerabilities. These allegations are consistent with the Framework’s guidance that companies should consider having a method for receiving threat and vulnerability information from information-sharing forums and sources.
Ultimately, much like the Framework’s Identify function, the FTC’s cases have sought to ensure that companies are taking reasonable steps to identify vulnerabilities and threats to determine the risk to consumers’ personal information.
Protect. The Framework’s Protect function provides guidance to help organizations develop and implement appropriate safeguards to ensure the delivery of critical services and to limit or contain the impact of a cybersecurity event. This includes limiting access to assets and facilities, raising employees’ awareness and providing training, managing consumers’ information consistent with the organization’s risk strategy, maintaining security policies and information security components, and using technical security solutions to secure systems and assets.
 Many FTC cases highlight companies’ alleged failures to implement reasonable data security practices that the Framework emphasizes under the Protect function. For example, in its action against Twitter, Inc., the FTC alleged that the company gave almost all of its employees administrative control over Twitter’s system. According to the FTC’s complaint, by providing administrative access to so many employees, Twitter increased the risk that a compromise of any of its employees’ credentials could result in a serious breach. This principle comports with the Framework’s guidance about managing access permissions, incorporating the principles of least privilege and separation of duties.
Many FTC cases highlight companies’ alleged failures to implement reasonable data security practices that the Framework emphasizes under the Protect function. For example, in its action against Twitter, Inc., the FTC alleged that the company gave almost all of its employees administrative control over Twitter’s system. According to the FTC’s complaint, by providing administrative access to so many employees, Twitter increased the risk that a compromise of any of its employees’ credentials could result in a serious breach. This principle comports with the Framework’s guidance about managing access permissions, incorporating the principles of least privilege and separation of duties.
The FTC’s cases against Accretive Health, Inc. and Cbr Systems, Inc. also comport with the Framework’s guidance relating to protecting data-in-transit and formally managing assets throughout removal, transfers, and disposition. In Accretive, the FTC alleged that an employee transported a laptop with personal information in a manner that made it vulnerable to theft or other misappropriation. Likewise, in Cbr Systems, the FTC alleged that the company created unnecessary risks to personal information by transporting portable media with personal information in a manner that made it susceptible to theft or misappropriation. In both cases, the laptops and the portable media were stolen, unnecessarily exposing thousands of people’s personal information. These cases demonstrate why companies should have reasonable security policies for when data is in transit or being transferred.
As shown, many of the FTC’s cases involve companies’ failures to develop and implement reasonable safeguards to protect consumers’ information—measures that also would fall under the Framework’s Protect function.
Detect. The Framework’s Detect function delineates various steps that organizations could take to develop and implement appropriate methods to identify the occurrence of a cybersecurity event in a timely manner. This includes monitoring information systems and assets at discrete intervals, and maintaining and testing detection processes and procedures to ensure timely and adequate awareness of anomalous events.
 The FTC has brought several cases that highlight why it’s important to have processes in place to detect intrusions. For example, in its action against Dave & Buster’s, Inc., the FTC alleged that the company didn’t use an intrusion detection system and didn’t monitor system logs for suspicious activity. Likewise, in Franklin’s Budget Car Sales, Inc., the FTC alleged that the company didn’t inspect outgoing Internet transmissions to identify unauthorized disclosures of personal information. Had these companies used tools to monitor activity on their networks, they could have reduced the risk of a data compromise or its breadth. Their alleged deficiencies also didn’t comport with the Framework’s guidance within the Detect function about monitoring networks for potential cybersecurity events or for unauthorized personnel, connections, devices, and software.
The FTC has brought several cases that highlight why it’s important to have processes in place to detect intrusions. For example, in its action against Dave & Buster’s, Inc., the FTC alleged that the company didn’t use an intrusion detection system and didn’t monitor system logs for suspicious activity. Likewise, in Franklin’s Budget Car Sales, Inc., the FTC alleged that the company didn’t inspect outgoing Internet transmissions to identify unauthorized disclosures of personal information. Had these companies used tools to monitor activity on their networks, they could have reduced the risk of a data compromise or its breadth. Their alleged deficiencies also didn’t comport with the Framework’s guidance within the Detect function about monitoring networks for potential cybersecurity events or for unauthorized personnel, connections, devices, and software.
Respond. The Framework’s Respond function provides guidance on how to develop and implement appropriate actions in response to a detected cybersecurity event to effectively contain its impact. This can include executing and maintaining response processes and procedures, coordinating with internal and external stakeholders, conducting analysis to ensure adequate response, containing and mitigating incidents, and incorporating lessons learned.
Many of the FTC’s cases have challenged companies’ failures to execute and maintain reasonable response processes and procedures. For example, in its case against Wyndham Worldwide Corporation, the FTC alleged that the company failed to follow proper incident response procedures, including failing to monitor its computer network for malware used in a previous intrusion. As a result of this and other failures, the FTC alleged that intruders were able to gain access to the company’s computer network on three separate occasions in a 21-month period, leading to the compromise of more than 619,000 payment card account numbers and more than $10.6 million in fraud loss.
 The FTC’s case against ASUSTeK Computer, Inc., demonstrates why it is important for companies to voluntarily share information with external stakeholders to achieve broader awareness of cybersecurity threats—guidance echoed by the Framework. According to the complaint, ASUSTeK learned of a variety of vulnerabilities affecting its routers. Despite this knowledge, ASUSTeK failed to provide adequate notice to consumers about these security risks, the steps consumers could have taken to mitigate them, and the availability of software updates that would correct or mitigate the vulnerabilities. As a result, hackers located consumers’ routers and exploited the vulnerabilities to gain unauthorized access to over 12,900 connected storage devices.
The FTC’s case against ASUSTeK Computer, Inc., demonstrates why it is important for companies to voluntarily share information with external stakeholders to achieve broader awareness of cybersecurity threats—guidance echoed by the Framework. According to the complaint, ASUSTeK learned of a variety of vulnerabilities affecting its routers. Despite this knowledge, ASUSTeK failed to provide adequate notice to consumers about these security risks, the steps consumers could have taken to mitigate them, and the availability of software updates that would correct or mitigate the vulnerabilities. As a result, hackers located consumers’ routers and exploited the vulnerabilities to gain unauthorized access to over 12,900 connected storage devices.
Several of the FTC’s cases have sought to ensure that companies not only detect breaches, but also take appropriate steps when a breach happens. This means that companies should contain events and communicate their occurrence with the appropriate parties. The Framework’s Respond function has a similar goal.
Recover. The Framework’s Recover function outlines steps organizations could take to develop, implement, and maintain plans for resilience and to restore capabilities or services that were impaired due to a cybersecurity event. It includes incorporating lessons learned into future activities, and coordinating with internal and external parties.
The Recover function supports a return to normal operations after a cybersecurity event. FTC orders demonstrate the importance of this function, emphasizing how consumer interests should factor into a company’s recovery plan. For example, in Oracle Corporation, the order required the company to provide broad notice to its users about the settlement and how to address Java vulnerabilities. Under the terms of the order, Oracle reached out to users not only through its website and social media, but also by working with external parties, such as antivirus vendors and browsers. This is consistent with the Framework’s guidance under the Recover function that organizations should consider communicating recovery activities with internal and external parties, including coordinating centers, Internet Service Providers, victims, and vendors.
How can a company use the Framework and the FTC’s Start with Security guidance?
The Framework’s five Core functions can serve as a model for companies of all sizes to conduct risk assessments and mitigation, and can be used by companies to: (1) establish or improve a data security program; (2) review current data security practices; or (3) communicate data security requirements with stakeholders. And as the FTC’s enforcement actions show, companies could have better protected consumers’ information if they had followed fundamental security practices like those highlighted in the Framework.
In addition, given that the FTC’s enforcement actions align well with the Framework’s Core functions, companies should review the FTC’s publication, Start with Security, which summarizes lessons learned from the FTC’s data security cases and provides practical guidance to reduce cybersecurity risks. Applying the risk management approach presented in the Framework with a reasonable level of rigor—as companies should do—and applying the FTC’s Start with Security guidance will raise the cybersecurity bar of the nation as a whole and lead to more robust protection of consumers’ data.
Note: video added to this blog on 3/13/2017
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0








